Alright, let's talk about something slightly different today. I've been digging into Scott J. Shapiro's book, "Fancy Bear Goes Phishing", and it’s providing some serious perspective, not just on cybersecurity, but on how we, as developers and tech professionals, often think about the systems we build and interact with.
Shapiro, who heads up the Yale CyberSecurity Lab, doesn't just give you a dry technical breakdown. He leans into narrative, much like authors such as Yuval Noah Harari do with history, using compelling stories of major hacks to illustrate deeper points. It's making me reconsider the whole concept of "solutionism" in our field.
Beyond the Code: Upcode, Downcode, and Metacode
One of the core ideas Shapiro introduces is the interplay between downcode (the actual software, the bits and bytes we write), upcode (the human systems: laws, social norms, economic incentives, psychological biases, corporate policies), and metacode (the fundamental principles of computation itself, like those Turing identified).
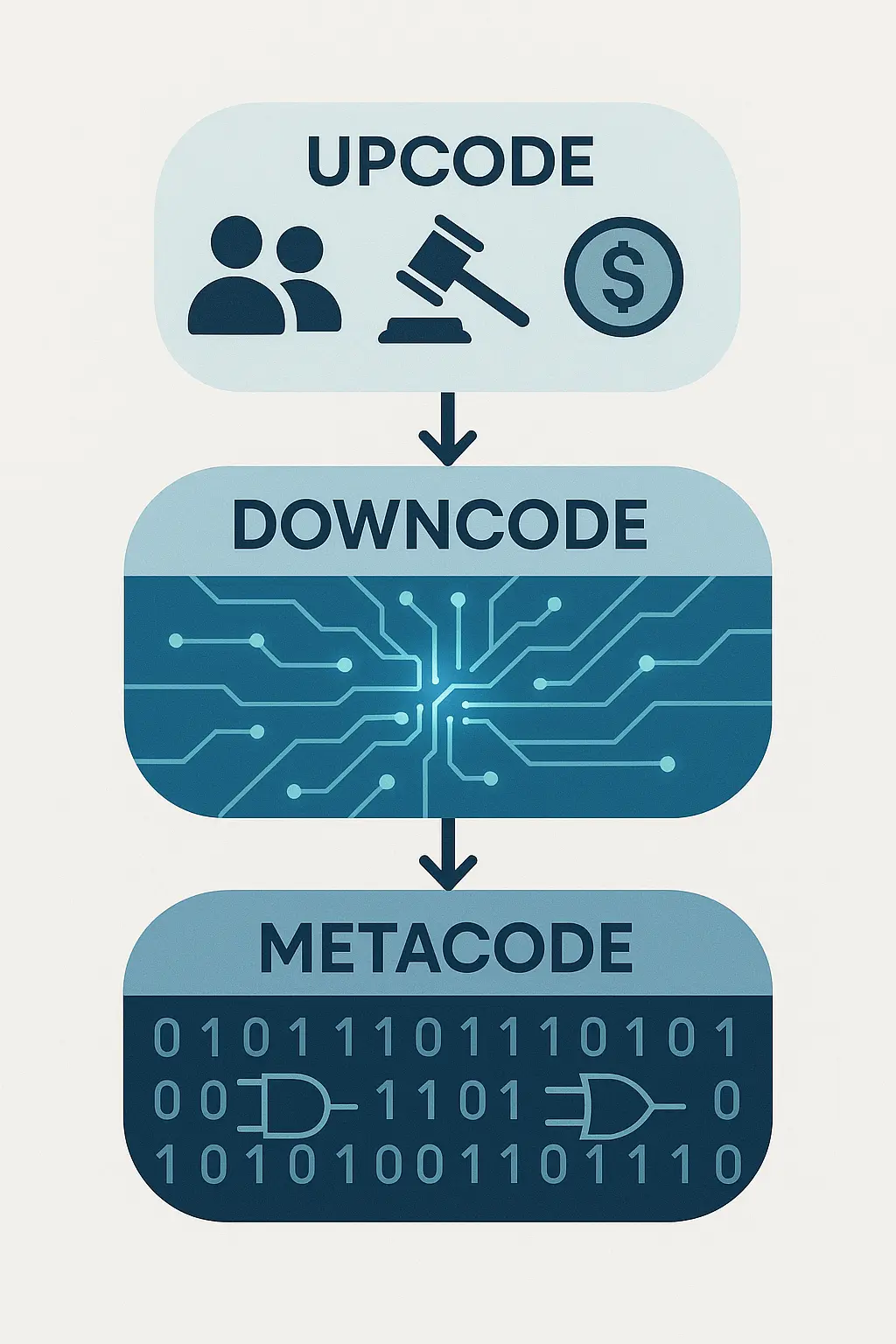 His argument, compellingly made through case studies, is that cybersecurity failures are rarely *just* about buggy
His argument, compellingly made through case studies, is that cybersecurity failures are rarely *just* about buggy downcode. More often, vulnerabilities arise from flawed upcode or clever exploitation of metacode.
Cybersecurity is not a primarily technological problem that requires a primarily engineering solution. It is a human problem that requires an understanding of human behavior. We need to pay attention to our upcode, determine where the vulnerabilities lie, and fix those rules so that we produce better downcode.
Narratives of Insecurity
The book walks through five major hacks, and the patterns are illuminating:
- The Morris Worm (1988): Not malice, but a grad student's experiment gone wrong due to a small error in the
downcode, amplified by the trusting 'academic sharing'upcodeof the early internet. It was a wake-up call about unintended consequences and led to the first US felony conviction under the Computer Fraud and Abuse Act. - The Bulgarian Virus Factory (~1990s): Driven by the
upcodeof a specific time and place – skilled programmers with few outlets, rampant piracy, lack of anti-virus laws. Figures like "Dark Avenger" emerged, creating technically sophisticated (and nasty) viruses likeEddie. - The Paris Hilton Sidekick Hack (2005): Less about technical brilliance, more about exploiting weak corporate
upcode(T-Mobile's lax security practices during market rush) and basic social engineering. A reminder that the human interface is often the weakest link. You can read contemporary news reports about the aftermath for the teen hacker and how social engineering played a key role. - The DNC Hack (2016): A state-sponsored operation (Russia's Fancy Bear group) using sophisticated
phishingthat exploited human psychology and organizational failures (like lack of mandatoryMFA) more than novel zero-days. CrowdStrike's analysis details the intrusion. - The Mirai Botnet (2016): Showcased the danger of insecure IoT devices. College kids built a massive botnet by exploiting default credentials in IoT
firmware– a glaringupcodefailure by manufacturers – causing huge DDoS disruptions. You can read technical analyses like Corero's overview or follow the latest news on Mirai variants.
Notice the theme? Technical exploits often succeed because of failures in human systems, psychological vulnerabilities, or fundamental computational principles (like the code/data ambiguity exploited in buffer overflows or SQL injections).
Debunking Cyber Myths & The Trouble with Solutionism
Shapiro pushes back hard against the typical media portrayal of hackers as omnipotent wizards and cyberwar as an imminent digital apocalypse. He argues malware is often hyperspecialized, and large-scale systemic attacks are much harder than portrayed. The biggest takeaway for me, as an engineer, is his critique of "solutionism" – the idea that we can engineer our way out of these problems with purely technical fixes.
If the
upcodepermits insecure practices (like default passwords on IoT devices, or companies facing no liability for data breaches), even the most sophisticateddowncodedefenses can be rendered useless. It’s like building an impenetrable fortress but leaving the keys under the doormat.
He argues persuasively that addressing cybersecurity effectively means addressing the upcode: improving laws, changing corporate incentives and culture, understanding user psychology, and even tackling the socioeconomic factors that drive cybercrime.
Practical Takeaways and Staying Sharp
So, while reading this, besides pondering the philosophy of it all, it's a good reminder of the fundamentals we sometimes neglect. We build complex systems, but often the breaches happen at the simple seams. This reinforces the need for:
- Solid Authentication: Seriously, enforce strong, unique passwords and push for Multi-Factor Authentication (MFA) everywhere possible.
- Input Sanitization: Remember the basics of preventing injection attacks. Never trust user input.
- Dependency Management & Patching: Keep systems and libraries updated. Outdated software is low-hanging fruit. The IoT landscape in 2024 still shows unpatched vulnerabilities are a major issue.
- Principle of Least Privilege: Does that service *really* need
rootaccess? - User Education: Phishing works. Training users (and ourselves!) to spot suspicious communications is vital. Use resources like the NCSC phishing guide.
- Secure Defaults: Build systems that are secure by default, not requiring users to be security experts just to be safe.
If you're looking to brush up on fundamentals or explore deeper, resources like CISA's best practices, SANS Cyber Aces, Coursera's cybersecurity courses, Cybrary, or TryHackMe offer accessible ways to learn.
Ultimately, "Fancy Bear Goes Phishing" is a compelling argument that securing our digital world requires more than just technical skill; it demands a holistic understanding of the human systems surrounding the technology. It's a worthwhile read for anyone building, securing, or just living within today's complex digital infrastructure.